Security teams face a critical challenge: how to choose the right combination of security tools to protect their organizations effectively. I’ve seen firsthand how organizations struggle with this decision, overwhelmed by the array of options available. With the rising sophistication of cyber attacks and the exponential growth of security alerts, the traditional approach of relying solely on SIEM or EDR solutions is no longer enough. Let’s decode the strengths and limitations of each tool to help you make informed decisions for your security stack.
The Evolution of Security Tools: Beyond Traditional Approaches
Traditional security approaches centered around SIEM and EDR have served us well, but they’re showing their limitations in today’s threat landscape. I’ll never forget working with a client who believed their SIEM and EDR setup made them untouchable, until an advanced threat exploited blind spots in lateral movement detection, something NDR excels at. That moment drove home a key lesson: cybersecurity isn’t about choosing one tool over another, it’s about choosing the right combination to close gaps.
Let’s Understand Each Tool’s Strengths
SIEM (Security Information and Event Management)
The foundation of many security operations, SIEM platforms excel at centralizing and correlating security data across an organization. They provide crucial capabilities for compliance reporting and historical analysis. However, their effectiveness diminishes when faced with advanced threats and encrypted traffic. Modern SIEM platforms attempt to address these limitations through integration with other security tools, but they still struggle with real-time threat detection and response.
EDR (Endpoint Detection and Response)
EDR solutions represent a significant advancement in endpoint security, offering deep visibility into endpoint behavior and automated response capabilities. They excel at detecting and containing threats at the endpoint level, but their scope is inherently limited. In today’s distributed environments, with remote work and cloud services becoming the norm, endpoint-centric security alone leaves dangerous blind spots in your security posture.
NDR (Network Detection and Response)
NDR technology fills critical gaps in modern security architectures. It provides comprehensive network traffic visibility, including the often-overlooked east-west movement within networks. A key advantage of NDR is its ability to detect fileless malware and zero-day threats through advanced behavioral analysis. Perhaps most importantly, NDR can monitor and protect unmanaged devices – from IoT sensors to BYOD equipment – that typically fall outside the scope of traditional security tools.
Which Tool for Which Threat?
To understand where SIEM, EDR, and NDR excel, let’s compare their coverage of key attack stages using the MITRE ATT&CK framework:
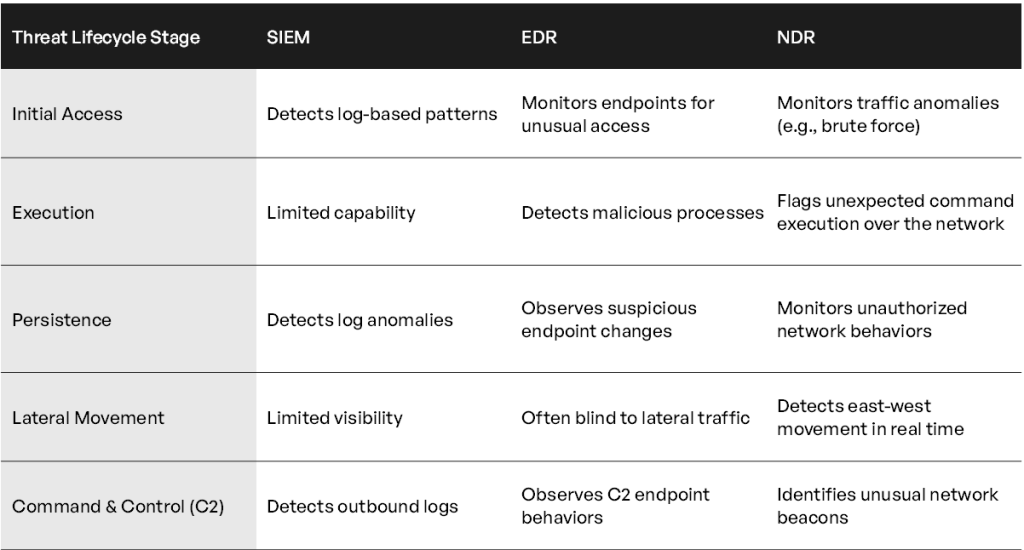
Each tool plays a distinct role but none can single-handedly cover all attack surfaces. SIEM is great at aggregating and correlating logs for compliance and historical analysis but struggles with real-time detection, particularly in dynamic or encrypted network environments. EDR delivers unparalleled endpoint visibility and response but leaves blind spots in unmanaged devices and fails to monitor network anomalies or lateral movement.
On the other hand, NDR focuses on real-time network traffic analysis, identifying advanced threats like fileless malware, ransomware propagation, and east-west movements – critical areas where SIEM and EDR often fall short. A layered defense strategy, where NDR complements SIEM and EDR, closes these critical gaps, ensuring organizations can detect and respond effectively across the entire threat lifecycle.
Why NDR Complements SIEM and EDR
Modern threats demand a layered defense strategy. SIEM, EDR, and NDR are not competitors; they’re complementary tools:
- SIEM provides a single pane of glass for logs and rule-based alerts.
- EDR focuses on endpoints with real-time monitoring, threat containment, and automated response at the device level.
- NDR closes gaps by monitoring network behavior, detecting threats SIEM and EDR miss.
By combining these tools, organizations can:
- Improve threat visibility across endpoints, networks, and logs.
- Detect anomalies in real time, including fileless attacks and ransomware.
- Optimize SOC workflows, ensuring faster and better incident response.
Real-World Impact and Implementation
Consider a manufacturing client we recently worked with. They relied solely on an EDR and SIEM setup for threat detection. During a recent ransomware incident:
1. The adversary bypassed endpoint agents using fileless malware.
2. Lateral movement across the network went unnoticed, spreading the ransomware to critical systems.
3. By the time the SIEM alerted the SOC team, the damage was done.
If NDR had been in place, it would have:
- Flagged the anomalous network traffic early.
- Detected the lateral movement within minutes.
- Enabled faster incident response, preventing the attack’s escalation.
Making the Right Choice for Your Organization
Selecting the right security tools requires careful consideration of your organization’s specific context. Environment complexity plays a crucial role – hybrid cloud/on-premise setups, legacy systems, and unmanaged devices all present unique challenges that require different security approaches.
Resource limitations are another key factor. Many teams face tight budgets and limited SOC capacity. That’s why modern security solutions need to prioritize automation and efficiency, helping your team focus on the real threats instead of drowning in alerts.
Next Steps: Building Your Modern Security Stack
The journey to enhanced security begins with a thorough assessment of your current position. Start by evaluating your existing security gaps and the effectiveness of your current tools. Consider how an integrated approach incorporating NDR capabilities could strengthen your security posture. Look for solutions that combine automation with expert support to maximize the value of your security investments.
In conclusion, the question isn’t whether to use NDR, SIEM, or EDR, it’s how to combine them effectively. Each tool has its strengths and limitations, and the right mix is what builds a strong, well-rounded defense against modern threats.
Ready to Enhance Your security Operations?
Contact our team for a comprehensive security assessment and discover how our Managed SOC solution can help you achieve:
- Sub-second threat detection and response
- 24/7 expert monitoring
- Complete coverage across your IT stack
- Automated threat mitigation